The peak holiday shopping season is upon us, and just as retailers are busy making the most of this time to turn a profit, so are cybercriminals.
By Imperva Area Vice President for Australia and New Zealand Tony Mascarenhas.

The sector is already experiencing challenges with the global supply chain crisis and an overloaded package delivery system. For some retailers, the impact of a single cyber-attack could be devastating.
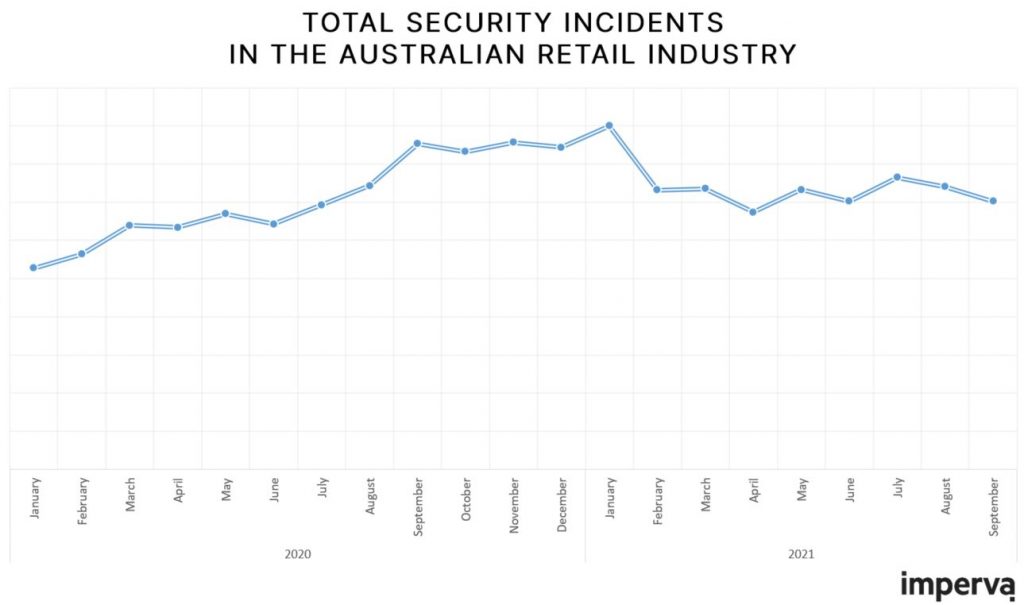
Imperva’s 12-month analysis on cybersecurity risks in the retail industry suggests that cybercriminals are increasing their efforts during a peak traffic season to create chaos for online retailers. Last year cybersecurity incidents in the Australian retail sector peaked from September 2020 through to January 2021. Retailers should expect the same to happen this year, but at a higher level. In fact, cybersecurity incidents are already 12% higher this year compared to the same period in 2020.
To help businesses prepare, I’ll highlight the three top cybersecurity threats facing the industry and how retailers can mitigate their risk.
Malicious bots
Online retail remains a prime target for automated bot activity in 2021. There are both good and bad bots. Good bots are used for productive purposes, such as for gathering data for search engines or price comparison services. Bad bots are used by a host of different actors to carry out both illegal activities (such as account takeover attacks) and quasi-legal activities (such as data scraping and denial of inventory) against retailers.
A majority (57%) of attacks recorded on e-commerce websites this year were carried out by bots, and the monthly volume of attacks is rising, up 13% from last year. Australia is one of the top targets for bot activity, ranking fourth in the world.
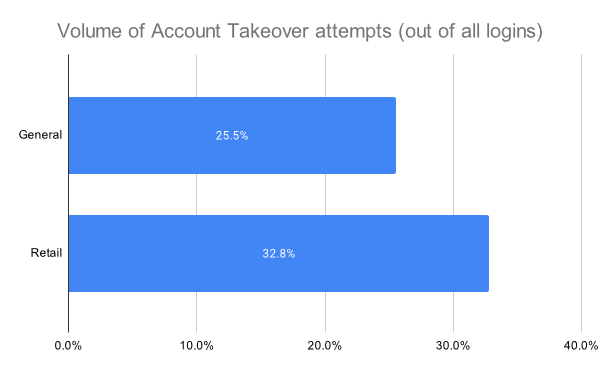
One of the most malicious bots – account takeover (ATO) – is particularly high in retail. This is where cybercriminals take ownership of online accounts using stolen passwords and usernames. This year ATO logins accounted for a third (32.8%) of all bot traffic in retail.
To help mitigate the risk of ATO, retailers should encourage their customers to practice good credential habits and safety, set strong password requirements and offer multi-factor authentication (MFA). They should also stay abreast of big data breaches that could impact their customers, and recommend users change their passwords after a breach has occurred.
Separately, use of inventory hoarding bots has increased during the pandemic and is causing friction for legitimate human customers. These bots generally target products that are scarce but in high demand. For example, Imperva Research Labs recently saw an 88% increase in bad bot traffic to global retail sites days before the launch of the Nintendo Switch OLED.
For this reason, online retailers need to be prepared to handle a high volume of traffic this shopping season and have a bot management solution in place only allowing legitimate customers into their websites. Otherwise, the makeup of traffic will include a high ratio of advanced bots that will hamper website performance and skew analytics.
Inventory hoarding bots can also cause retailers to lose customers and revenue, and damage brand reputation. If a retailer doesn’t have the product a customer wants, they quickly go to a competitor’s site. Once gone, they may never return. Consumers can also be quick to blame the retailer for stock shortages. For example, when the launch of a new GPU sold out in just 1.2 seconds, consumers took to Twitter to express their outrage.
Website attacks
Many websites have web application vulnerabilities that can be exploited by cyber criminals to manipulate source code, collect sensitive data or gain unauthorised access.
This time last year, Imperva saw that attacks on retail websites were notably higher than all other industries. In Australia, the top three web application attacks in retail in the past year were Data Leakage, Remote Code Execution (RCE) / Remote File Inclusion (RFI) and Cross Site Scripting (XSS).
Common applications targeted by such attacks are online forms and JavaScript-based services including Live-Chat services and payment gateways. These attacks are commonly referred to as Magecart attacks. Retail websites are particularly vulnerable to these attacks because retail websites have more JavaScript-based services executing on the client-side than any other industry. The volume of JavaScript plugins in retail has doubled in the last 12 months, creating greater opportunity for exploitation.
Magecart style attacks are notorious for making use of compromised first or third-party JavaScript to exfiltrate sensitive information out of website forms such as login and checkout. Targeting e-commerce sites that experience a lot of transactions, especially during peak shopping periods, is an ideal strategy for attackers.
To mitigate risk, retailers need to ensure their existing website functionalities are protected and ensure newly added ones are secure too. It is a good idea to take inventory of all your client and server-side JavaScript-based services. Consider using a specialised tool that can help in identifying and assessing the risks of each JavaScript-based service, as well as enabling you to block unauthorised ones from executing.
DDoS attacks
Australian retail is a prominent target for application layer (layer 7) DDoS attacks, ranking third in the world in 2021.
Throughout the past 12 months, the retail industry experienced the highest volume of application layer DDoS incidents per month of all industries, and in September 2021, Imperva Research Labs saw a 200% spike over the previous month. The increased level of attacks shows that threat actors are ramping up for the peak shopping season.
Peak shopping days such as Boxing Day are favorite times for attackers to launch DDoS attacks at online retailers. Therefore, retailers should stress-test their infrastructure regularly, and ensure they are properly protected against DDoS attacks across all web resources, including DNS.
The end-of-year period is always particularly busy and stressful in the retail industry. However, it is important that you don’t let cybersecurity fall by the wayside. As recent history has shown us, the holiday period is a ‘perfect storm’ for bad actors to make mischief for online retailers, so this is a time for strengthening your security posture. Retailers that stay ahead of the cyber risks that are threatening the integrity and continuity of their business this shopping season will be the ones that survive and thrive in 2022.
About Tony Mascarenhas
Tony Mascarenhas is the Area Vice President for Australia and New Zealand at Imperva. He has more than 25 years’ experience managing, selling and consulting to various industries including retail across Australia, Asia, America and Europe. Tony’s strong customer relationships and understanding of their business has enabled him to match the right enterprise technology solutions to solve their unique business challenges.
About Imperva
Imperva is the cybersecurity leader that helps organisations protect their data and all paths to it. Customers trust Imperva to protect their applications, data and websites from cyber attacks. With an integrated approach combining edge, application security and data security, Imperva protects companies through all stages of their digital journey.





